Getty Images
Market-leading garage door controllers are so full of serious security and privacy vulnerabilities that the researchers who discovered them immediately disconnected everyone using them until they were fixed. I advise you to do so.
Each $80 device used to open and close garage doors, control home security alarms, and control smart power plugs uses the same easy-to-find universal password to communicate with Nexx servers. The controller also uses unencrypted e-mail addresses, device IDs, first names, and corresponding last initials to open/close doors, turn smart plugs on or off, or schedule such commands. Broadcast with the desired message. time.
Remove all Nexx devices immediately
As a result, anyone with a moderate technical background can look up a specific email address, device ID or name on the Nexx server and issue a command to the relevant controller. (His Nexx controller for home security alarms is susceptible to a similar class of vulnerabilities.) Commands allow you to open doors, turn off devices connected to smart plugs, You can cancel the alarm. To make matters worse, in the past three months, his Texas-based Nexx rep has not responded to multiple private her messages warning of the vulnerability.
“Nexx consistently ignored communication attempts from myself, Homeland Security, and the media,” wrote the researcher who discovered the vulnerability. Post published on Tuesday“Device owners should immediately unplug all Nexx devices and create a support ticket asking the company to fix the issue.”
Researchers estimate that over 40,000 devices in residential and commercial properties are affected and over 20,000 individuals have active Nexx accounts.
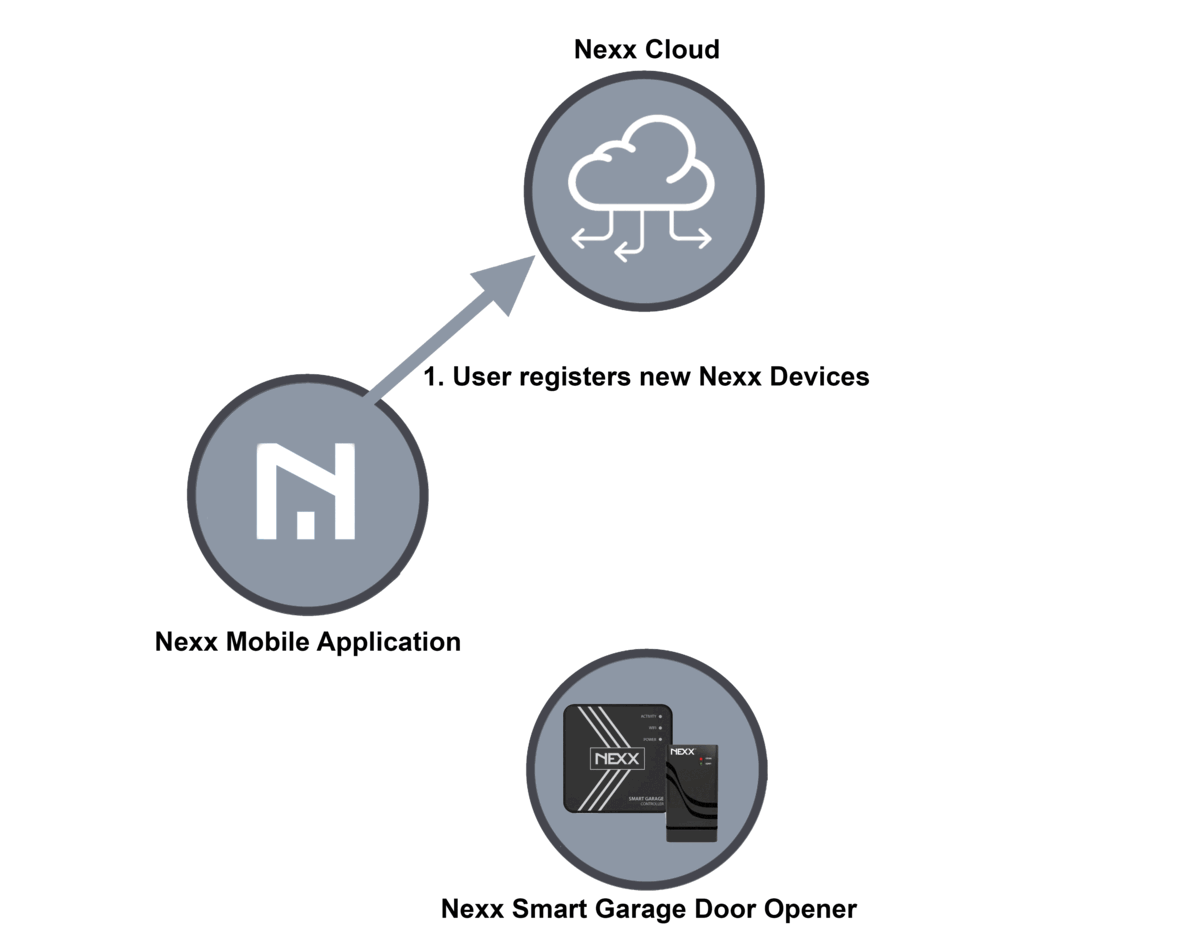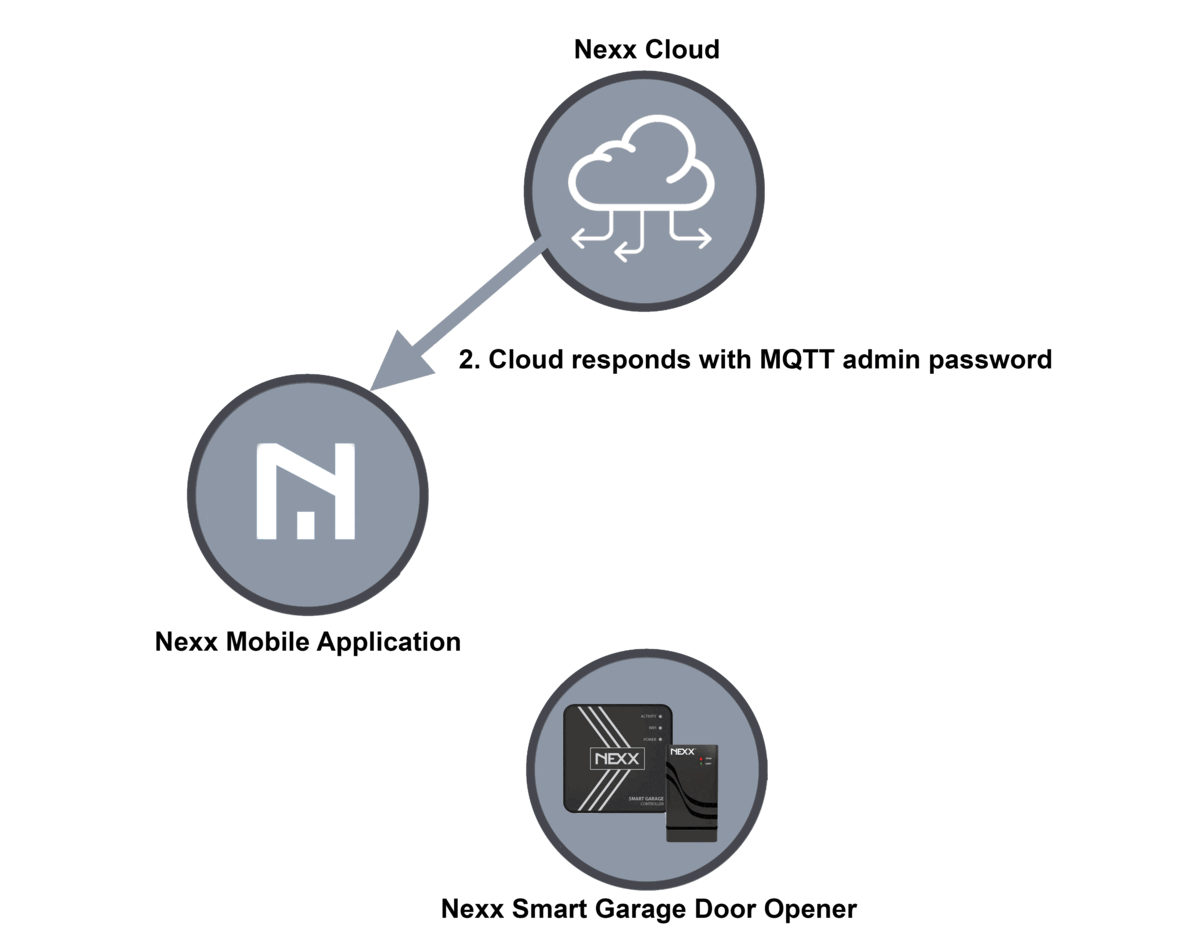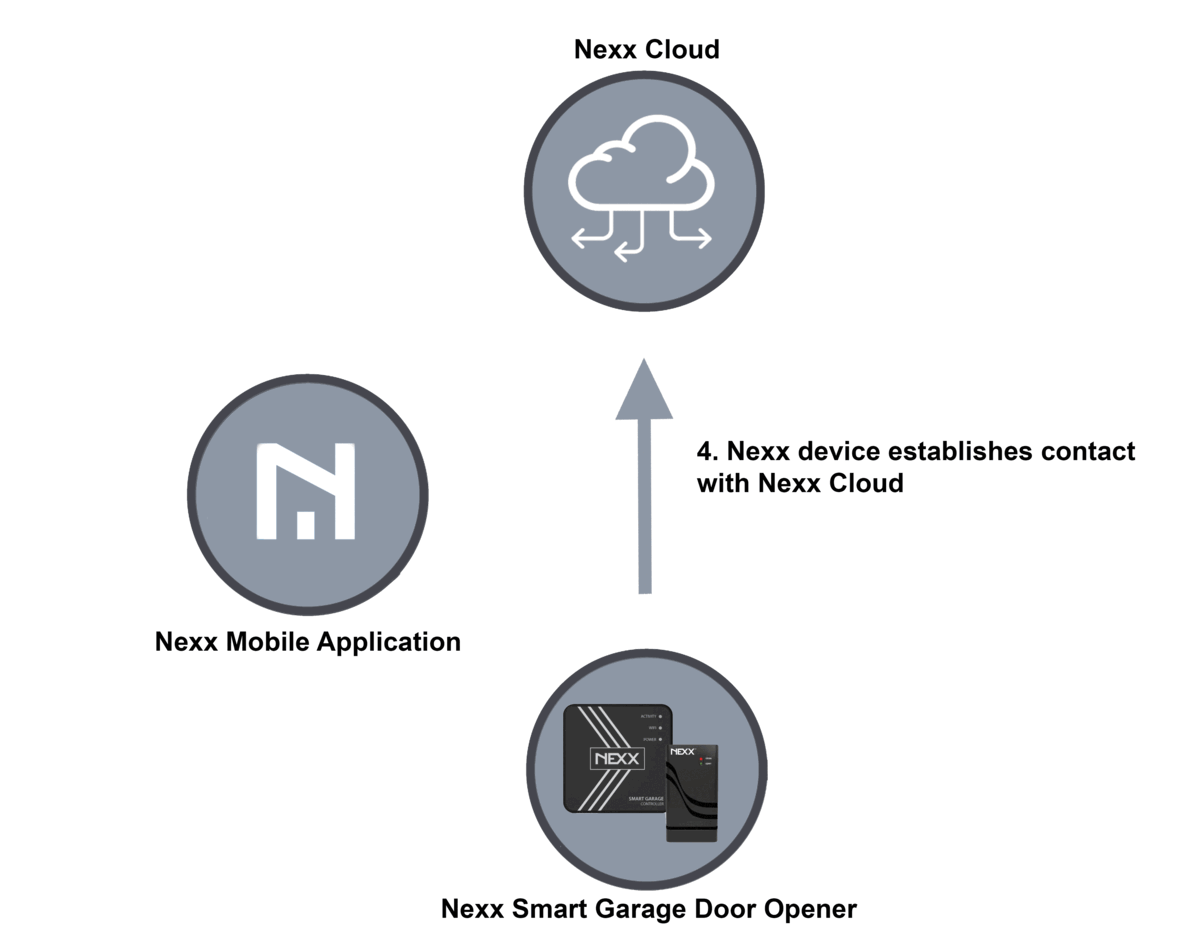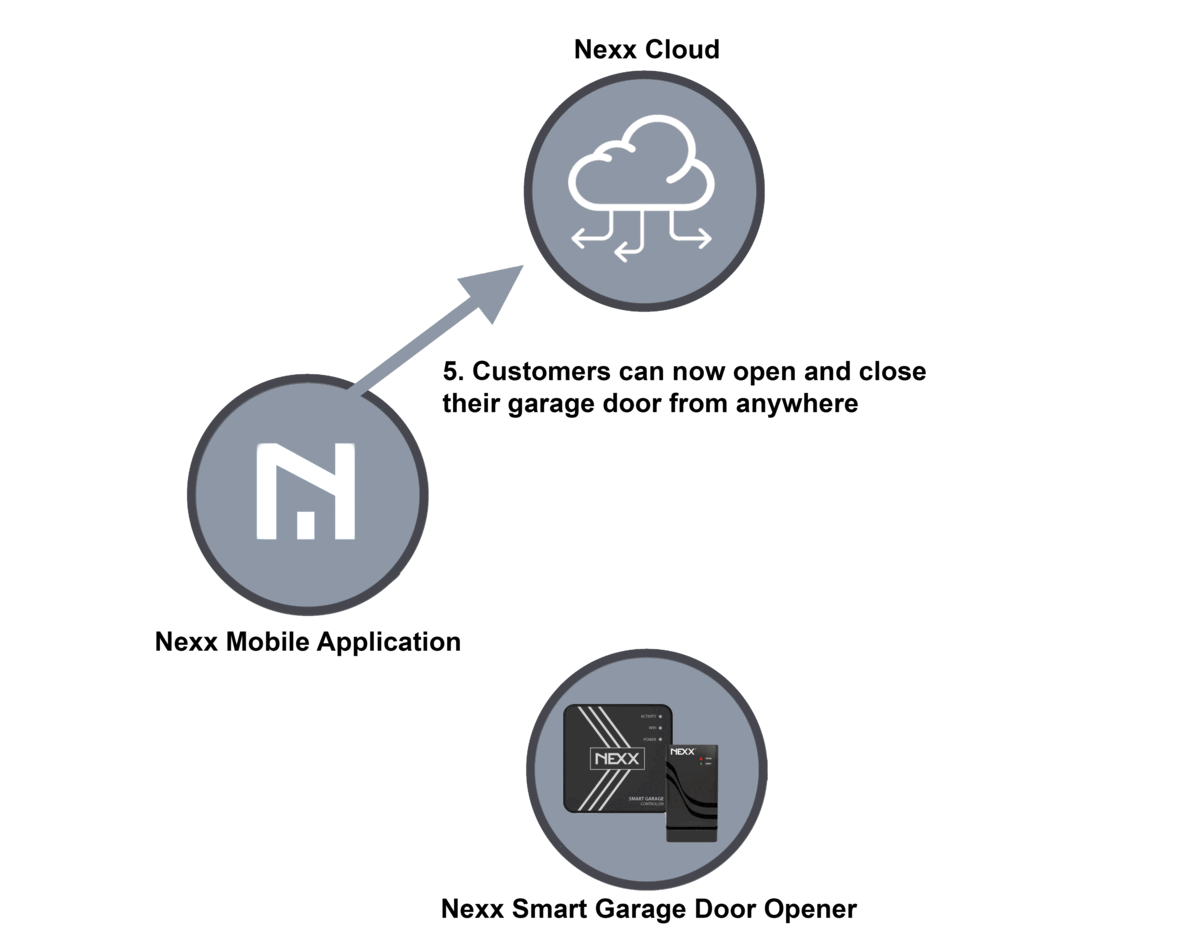
With the Nexx controller, you can use your phone or voice assistant to open and close your garage door on command or at scheduled times. These devices can also be used to control home security alarms and smart plugs that turn appliances on and off remotely. The hub of the system is a server operated by Nexx that both the phone or voice assistant and the garage door opener connect to. The five-step process for registering a new device looks like this:
- Users register new Nexx devices with Nexx Cloud using the Nexx Home mobile app.
- In the background, the Nexx Cloud returns a password that your device uses for secure communication with the Nexx Cloud.
- The password is sent to the user’s phone and sent to the Nexx device using Bluetooth or Wi-Fi.
- The Nexx device will establish an independent connection with the Nexx Cloud using the password provided.
- Users can now operate their garage doors remotely using the Nexx mobile app.
Here is a diagram of the process:
Sam Sabetan
Easy-to-find Universal Password
To make all this work, the controller uses a lightweight protocol called MQTT. Short for Message Queuing Telemetry Transport, it is used over low-bandwidth, high-latency, or otherwise unstable networks to facilitate efficient and reliable communication between devices and cloud services.To do this, Nexx uses Publish-to-subscribe modela single message is sent between a subscribed device (phone, voice assistant, garage door opener) and a central broker (Nexx cloud).
Researcher Sam Sabetan found that the devices used the same password to communicate with the Nexx cloud. Moreover, this password can be easily obtained by simply analyzing the firmware that ships with the device or the interaction between the device and his Nexx cloud.
“Using a common password for all devices creates a significant vulnerability as unauthorized users can obtain shared passwords and gain access to the entire ecosystem,” the researchers wrote. “By doing so, they could compromise not only the privacy but also the safety of his Nexx customers by controlling the garage door without their consent.”
When Sabetan used this password to gain access to the server, he immediately saw not only communication between his device and the cloud, but also communication between other Nexx devices and the cloud. This meant that we were able to sift through other users’ emails, his address, last name, first initial, and device ID to identify the customer based on the unique information shared in those messages.
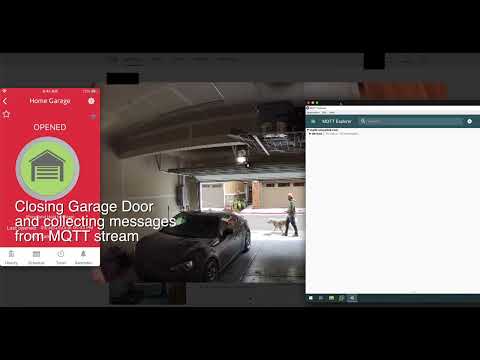
But it gets even worse. Sabetan was able to copy messages issued by other users to open doors and play them freely from anywhere in the world. A simple cut-and-paste operation was enough for him to control his Nexx device wherever he was.
Here’s a proof-of-concept video showing the hack:
NexxHome Smart Garage Vulnerability – CVE-2023-1748.
The event brings to mind the clichéd cliché that the S in IoT stands for security. Many IoT devices offer convenience, but many are designed with minimal security protections. Outdated firmware with known vulnerabilities and inability to update is common, as are myriad flaws such as hard-coded credentials, authentication bypass, authentication verification failures, and more.
Anyone with a Nexx device should seriously consider disabling it and replacing it with something else, but there is no guarantee that the alternative is more secure, so the usefulness of this advice is Limited.
With so many devices at risk, the US Cybersecurity and Infrastructure Security Agency Recommendation This suggests that users take protective measures such as:
- Minimize and ensure network exposure of all control system devices and/or systems not accessible from internet.
- Place control system networks and remote devices behind firewalls to isolate them from business networks.
- If remote access is required, use secure methods such as a virtual private network (VPN). Please be aware that your VPN may have vulnerabilities and should be updated to the latest version available. Also, realize that a VPN is just as secure as the device it’s connected to.
Of course, deploying these countermeasures is not possible when using Nexx controllers. This brings us back to the whole IoT anxiety and Sabetan’s advice to simply throw the product away unless or until a fix arrives.